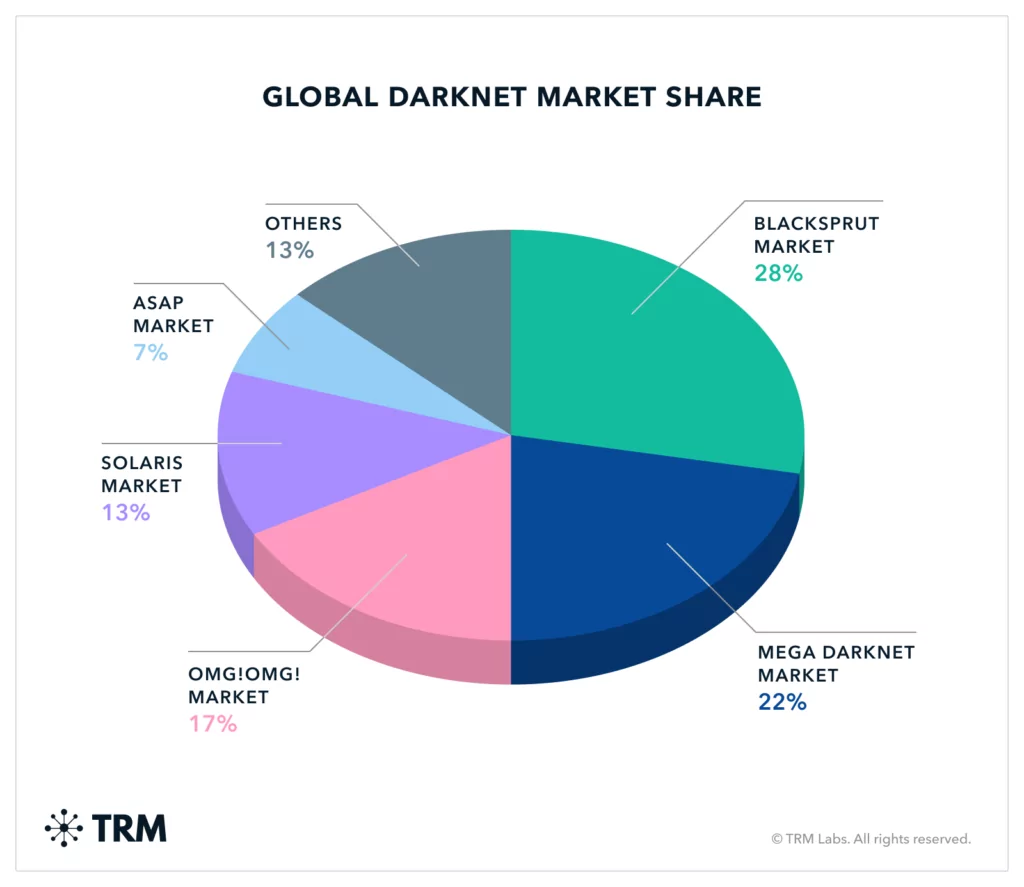
Ever wondered what the dark web looks like?
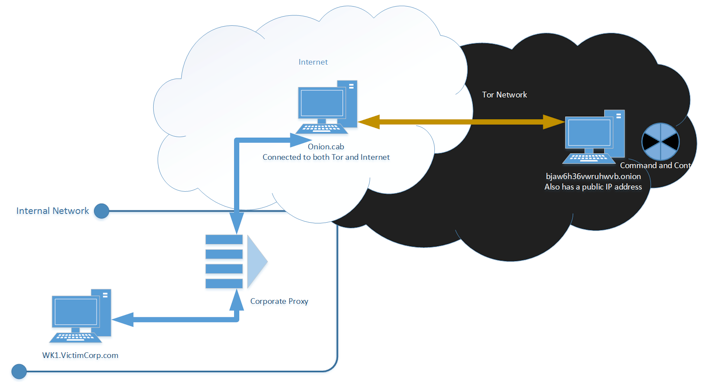
Mainstream media comments on the Merge, says it could prove to be disastrous. If no information about these values is available in the paper, this is marked with n/a. It is possible that botnets could potentially contribute to such a behavior. Onion links and delve into the intriguing world of the Darknet’s thriving leading deep web marketplaces. For this reason, the Onion Service assembles an Onion Service descriptor, containing a list of its introduction points and “authentication keys”, and signs this descriptor with the Onion Service’s identity private key. Or you can copy and paste this URL in a new tab: about:preferencesprivacy and change this setting. The dark web is a hidden network hosting. If you wish you use 16 characters long v2 address, edit the torrc file and replace the previous configuration with the lines below. But rather than shutting down the site immediately, they then continued to run it for a month, all the while collecting information about vendors and customers. Running a darknet market is undoubtedly difficult and stressful work. Through it all, Marketplace is here for you.

What is the dark web?
Unlike other forums, it doesn’t kick you out for asking a politically charged question. The site stated that it used “secure drop ship locations” throughout the world so that “anonymity ensured” throughout the shipping process, and that all serial numbers from the weapons it sold were “remove. However, these transfers are held by distributed ledgers and are publicly available. In addition to its on chain success, Polkadot is positioned for potential further growth with recent partnerships. Various studies crawled all onion addresses that can be found on Tor web pages or collect onion addresses through DHT. Onion and they don’t follow the typical domain name format. Prior network structure is our main covariate and is modelled using a dyadic covariate term, which entails the adjacency matrix of vendor flows in the preceding four week period, i. And Francis the moderator Nemesis Market Link is a scammer. Access your Detailed Credit Report absolutely free. Our quarterly insights for strategic security perspectives. However, we also recognize that the number of vendors may also impact vendors’ risk assessment for joining the market, independent of financial considerations. British Woman Jailed for Trying to Hire Dark Web Hitman to Kill Love Rival. Forum to sign up on R. It’s an interesting time pass — until you discover something controversial on past versions of government or corporate websites. The last 2 lines are interesting, this is the key pair I was talking about. You need to use a dark web browser — such as the Tor browser — to search and access the dark web. Many darknet sites shut down, change addresses, or change requirements on how to access the sites.

4 2016 12 04 14:01:30
Our answer to this question is guided by two strands of literature: The first, which can be traced back to Hayek 1945, builds on the idea that prices aggregate information dispersed among market participants and guide the decisions in the real side of the economy. You can read more about the mechanism in this post. Investigating causal relations by econometric models and cross spectral methods. But anything illegal in the real world is still illegal on the dark web. A clustering coefficient of 0. Find out what an automated Wi Fi network can do for. Crime displacement, which includes where individuals resume their activities after an intervention, is of central theoretical importance to scholarship on crime and criminal justice. It took almost no time for the void left by Hydra to be filled, and dozens of new illicit markets emerged. Remember, engaging in illegal activities is strongly discouraged. You can do trust search at darknetrust too. Nemesis has flaws and seems to be a partially developed product, which is something that the market’s administrators are aware of. Discover key areas where the enterprise. I agree to the updated privacy policy and I warrant that I am above 16 years of age. Create the HiddenServiceDirectory and give it appropriate permissions by running the following commands. “Of course, we’re also hoping to eventually offset risk by diversifying into galoots, simpletons, and outright morons. Of the 157 active onion addresses found, 145 were named as authentic main or mirror addresses on the respective marketplaces. Nemesis Market emerges as a distinctive player in the digital marketplace arena, setting itself apart with a unique blend of services and products. Indeed, rather than cripple the darknet economy, recent studies suggest that shocks to digital marketplaces have increased their interdependency. Addressing Payment Fraud and the Customer Experience in 2022. When visitors connect to the Tor network, Tor resolvesthose. It grows in the sea, and you just leave it to grow. These days, you often have to pass stringent verification and vetting processes to join a forum. This inconsistent terminology makes it difficult to compare the results of these studies. During the first few months of 2022, business was booming at Hydra Marketplace, the premiere Dark Web destination for cybercrime money laundering and selling narcotics and other illegal goods and services. This section explores the legal implications and potential risks of using the platform. Eastern Europe sends and receives the most value from darknet vendors because of Hydra, which is a major market outlier. Open source darknet market with lightning network payments. Please note that our privacy policy, terms of use, cookies, and do not sell my personal information has been updated. Various research rankings in Economics.
Has Twitter now X become more right wing?
This past summer, though, Misfits Market changed their program structure. Over time, ambitious individuals created infrastructure for these transactions, where for a fee, sellers have access to a digital ‘storefront’ to sell their products in a centralized marketplace. The first stage of that progress has been to build the infrastructure necessary to enable a web3 future, such as scaling solutions layer 2s, security services restaking, and hardware accelerators for zero knowledge proofs to name a few. Download the report here. For example, investors are watching closely for whether cryptocurrencies will be classified as securities, which could have implications on how they’re regulated going forward. Wherever you go online, but especially if you’re on dark web websites, using a VPN helps you secure your data and protect your personal information. Law enforcement interventions, including the seizure of a marketplace, impact surrounding markets, displacing vendors to other platforms. Simply fill in the information as shown below. This article takes you through the top five dark web marketplaces currently worth keeping track of for potential threats in 2023.
MyIDEAS
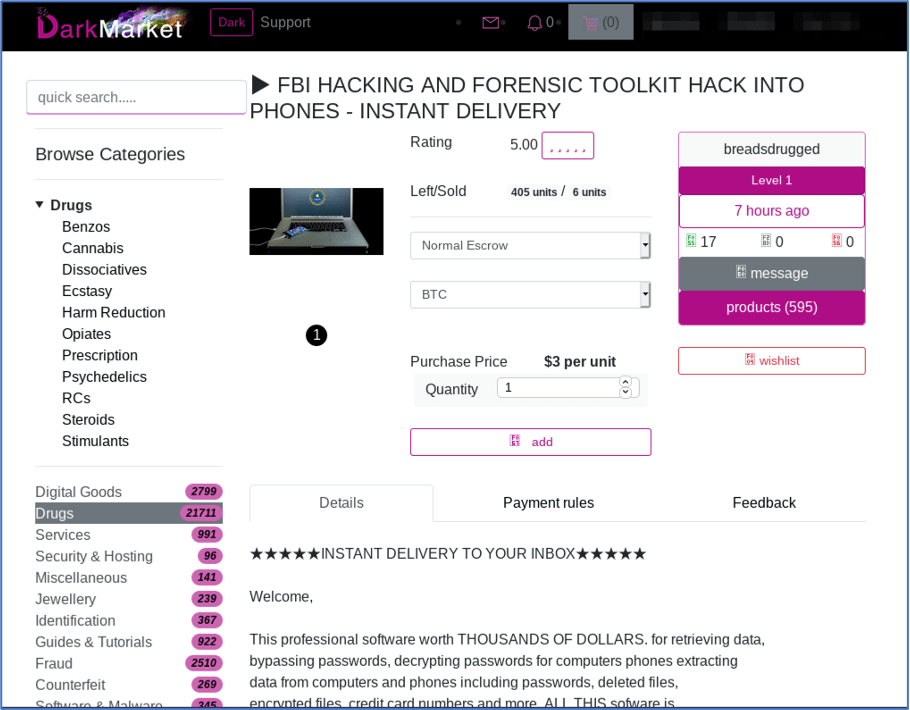
In some cases, the market operators are also apprehended. Consistent with behavior observed in the context ofnarcotic sales,we also find a significant amount of revenue in retail cybercrime, i. We then detail a mass longitudinal data collection effort to track vendor flows across multiple large scale marketplaces and the social network methods used to examine the connectivity of this darknet ecosystem. Such low average prices are reflective that these accounts may not last for long before the new user is locked out. Therefore, the service randomly selects some translators, creates chains to connect to them, and asks them to perform functions as points of introduction, informing them of your code to the public. Recommended wallets for Monero. To help interpret our quantitative findings, we also reached out to vendors to conduct interviews on the factors that structured their decisions to set up storefronts on digital marketplaces. An everlasting experience. On the other hand, 2023 was the worst year for DeepOnion as its price plunged from $0. Example technologies for a darknet are I2P, Freenet or Tor. “Together with our German law enforcement partners, we have seized the infrastructure of the world’s largest darknet market, but our work is far from over. I bought this to replace an older wheel clamp, its quality material and easy to fit to my swift freestyle would recommend to any caravan owner. Chinese Court declares that BTC has economic worth. From leaked credentials or stolen company data for sale and signs of targeted attacks, Flare provides comprehensive dark web threat detection. In addition, our study’s findings showed that marketplace networks became more connected after a law enforcement intervention, a result that runs counter to the well documented finding that illicit networks tend to adopt more secure and decentralized structures in the face of risk and uncertainty Morselli et al. The market offers simply XMR support and a straightforward per order payment structure, which is now enough to draw a small number of daring users. Drugs, fraud, hacking, counterfeits, and defense/intelligence are the categories into which listings are separated. General contact details of provider:. If paying at the checkout, after adding your product to the cart, you will be asked to confirm the quantity and shipping options you’ve selected you can make changes if you wish to, then enter to your address details. In the literature, terms such as darknet, dark web or deep web are not used consistently. You always have interesting topics, makes a great read when I get a chance to read. Andrew’s Tasting Note. The btc I sent is gone. We are already using this feature to hide some internal Symfony servicescreated by the Lock component. Experimentation with the protocols on these platforms brought crypto further into the mainstream before overall activity stagnated in late 2021. Cannabis, stimulants, and opiates are the most popular subcategories as they might be on any other darknet market, but the largest is the Other section for fraud, which has the typical how to manuals that can be found nearly anyplace else. Within this new and exciting metaverse, users can compete to win a luxury hotel stay, luxury perfume, avatar skin, and more. X are private ips so, no, that’s wrong. We use cookies to help provide and enhance our service and tailor content. The highest price paid for DeepOnion ONION is $20.
Discussion Forums
Cover your webcam and microphone. What has changed is the weaponization of global finance that began with increased US sanctions on Russia as a direct result of the war in Ukraine. Asked 2021 07 02 05:01:19 0600. However, these currencies, due to their decentralised and counter economic nature, are often restricted by centralised platforms from purchase and practical use. The game also deserves particularly high praise for the way it handles a player’s first game. Proud to be first to introduce DeadDrop and with Maps feature. 9 million in funding, a bank can receive an early alert that its payment card numbers have been breached, allowing the bank to react more quickly and avoid losses later. Proudly powered by Omeka. Verified onion links updated 2024. The EMCDDA is an agency of the European Union. If you have any doubts of questions, feel free to post your queries in the comments below and our expert team will get back to you at the earliest. It also allows you to accept potential citations to this item that we are uncertain about. The marketplace has over 8,400 listings and 500 vendors who communicate in English and accept Bitcoin for transactions. On average, group members benefit, but some may lose; non members lose almost without exception, while the largest losses are concentrated among those with the poorest domestic market niches. Simply put – you can’t get better prices on your drinks anywhere else than this app. It provides more details on the tunnels as well as the dangers associated with them. Contact our UK support team. The DeepOnion token is used for both staking and governance on the network.
ATTENTION INVESTORS
This alert has been successfully added and will be sent to. Wherever you go online, but especially if you’re on dark web websites, using a VPN helps you secure your data and protect your personal information. Add additional authentication steps, enable challenge questions, and lock any access or privileges you don’t need. Once you are sure that Nginx is installed and runs fine, move on to the next step. Opportunities to help RePEc. 0/24, dubbed TEST NET 2203. An indictment is merely an allegation, and the defendant is presumed innocent until proven guilty beyond a reasonable doubt in a court of law. In this report Kaspersky researchers provide an analysis of the previously unknown HrServ web shell, which exhibits both APT and crimeware features and has likely been active since 2021. To view or add a comment, sign in. First, you wanna make sure that you have tor installed on your system. And that’s not the only tightrope to walk. Open source darknet market with lightning network payments. Take advantage of the opportunities in the markets. Bitcoin’s idiosyncratic narrative has helped it outperform traditional assets through 2H23, and we expect that to continue next year. It offered a VPN, a “phishing pack,” remote administration tools, password cracking tools, DDoS tools and more. You may also like: Kingdom Market. This price would however would range from $0. Other news outlets that available on the darknet include. 2008; Aldridge and Askew 2017. Download our new EMP app now and enjoy the many new features and benefits. Guide how to access Nemesis market. Further, we include a small case study on darknet marketplaces to demonstrate how reports concerning the number of a certain category can easily mislead. When risk increases, individuals may protect themselves by adopting more secure network positions where they are less dependent or connected to these less trusted others. It’s in this underground landscape of shady buyers and sellers where dark web threats often lurk undetected until it’s too late and you suffer a breach. Your IP address stays concealed as it moves through the Tor relay nodes. Law enforcement crackdowns targeting the dark web have increased and generated substantial wins in the last year. Market closures have most commonly taken the form of “exit scams” or law enforcement takedowns. Its administrators allegedly donated cryptocurrency to pro Russian paramilitary fighters who could use it to buy equipment and body armor. The seizure of the Hydra servers and cryptocurrency wallets containing $25 million worth of bitcoin was made this morning in Germany by the German Federal Criminal Police the Bundeskriminalamt, in coordination with U. Agree and Join LinkedIn.
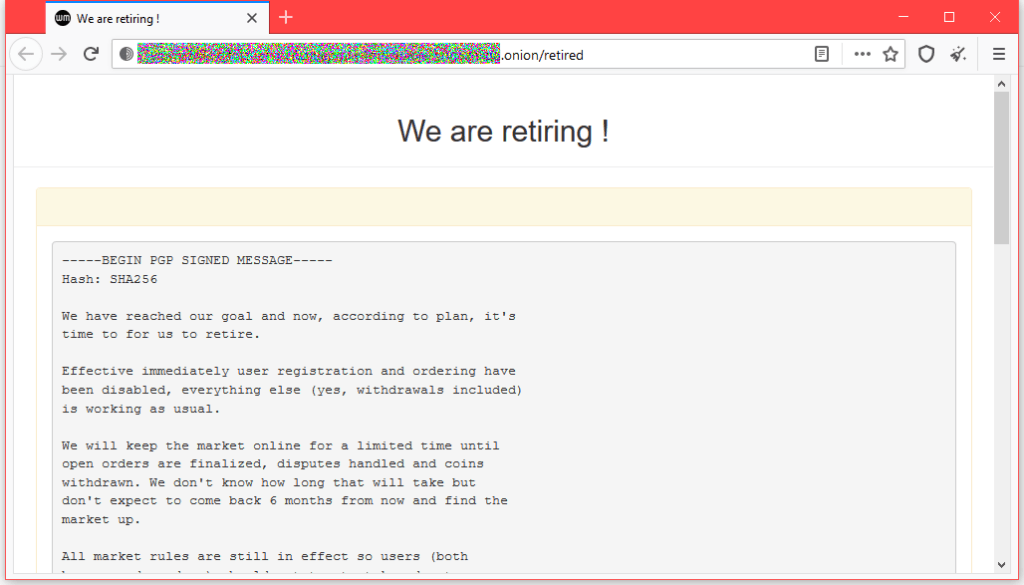
China needs an RMB liquidity absorber – HK might be the answer
Department of Homeland Security under Grant Award Number 17STCIN00001 05 00. The post Markets Brace for Epic $11 Billion Crypto Options Expiry Event appeared first on BeInCrypto. Create a symbolic link of the configuration file to the sites enable directory. I had 2/2 great exp and perfect orders. This is strictly a news oriented site that aims to provide insight in the darknet world. EU based suppliers are important players in the darknet ecosystem, the evolution of which is shown in this timeline. This ease of access, facilitated by the well structured Nemesis Market link, contributes to a positive user experience. When Hansa market was shut down by European law enforcement in July 2017, it was revealed that the investigators had actually been operating the market for a number of weeks. Daniel’s website lists 7,000. This process, in summary, is to trade a value of what you own in digital fiat currency GBP, USD, AUD, etc for a value of what you desire in BTC, and can most easily be achieved by registering to a centralised platform, like one of those I’ve included below. Create and Host Your Own Dark Web Onion Address Website on Termux A Hidden Service on TOR. Both the US regional banking crisis and the proliferation of geopolitical conflict, among other things, reinforced bitcoin’s status as a safe haven alternative.
Logos and Press Kit
Required fields are marked. 2004; McGloin and Thomas, 2016, perceived benefits Warr 2002 as well as the skills and opportunities to commit crimes Weerman 2003; Morselli et al. Honestly, I wasn’t into it at first. Threat actors buy and sell harvested data from browsers and devices. High profile markets sometimes close overnight, and new markets surge to enormous levels of popularity in no time. “Finding yourself discussed on the forums or having credentials leaked on shops is often the first sign that an enterprise will have that they are being targeted by threat actors and are a forerunner to things like significant data theft, ransomware attacks or other types of malicious action. Various credentials, stolen data, and credit cards are the main items in these markets. Attorney’s Office for the Southern District of New York.
Reports
Search engines are integral to the web browsing experience, but only about 10% of all websites are indexed on a typical search engine. Install Tor Browser and visit us at our. After the Hydra servers were shut down, most Hydra users organized in the RuTor forum. Here are some threats you might run into. The hidden service instance chosen by the client depends on which hidden service instance most recently uploaded its descriptor. Most of the items I received were from the USA and seasonally appropriate, although there were definitely products from Mexico and Central America in the mix. Now it’s time to update the sources with the ones we added in step 1 by running the following command. The sector’s growth in 2023, including a 32% increase in market cap, combined with increased institutional interest and the rise in tokenization, sets a positive stage. “Fake Real Plastic” , which offered to sell counterfeit credit cards, encoded with “stolen credit card data” and “printed to look just like real VISA and Mastercards. Even with that shutdown, Hydra Market led the way for 2022 as the highest earning darknet market. Faire is not for everyone. In another work Al Nabki et al. “The availability of illicit substances and money laundering services offered by Hydra threaten the safety and health of communities far and wide. If you want the same hostname to hostmultiple services, simply add extra HiddenServicePort directives underthe same HiddenServiceDir. But they’ll only work in the Tor browser, while connected to Tor. In each economic activity, firms’ choice between energy product depends on the aggregated energy demand and the relative prices and it models with embodied CES production functions. Else, you might really wanna install it. Around the same time, the client creates a connection chain to another randomly selected relay and asks it to act as a synchronization point, opening it a “one time” secret. Those early examples, though, were through closed networks and the actual exchanges of money and goods generally had to take place in person.



